If You Own A QNAP NAS That May Have Be Exposed to The Hack, Check It Now and Block All External Access Until You Are Sure the Firmware and Apps Have Been Updated.
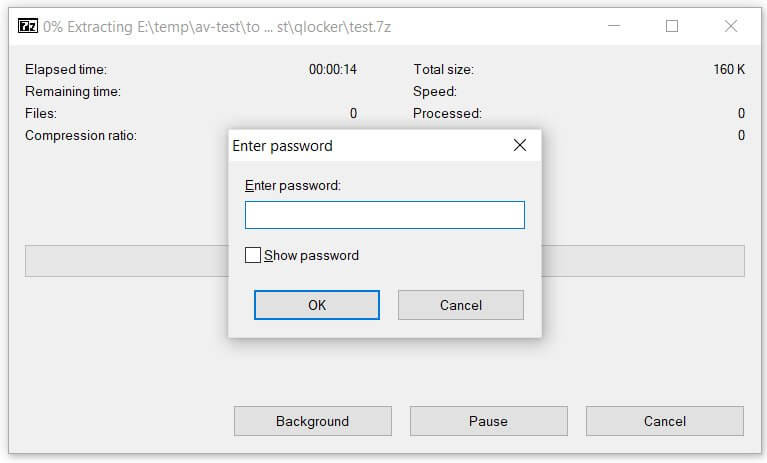
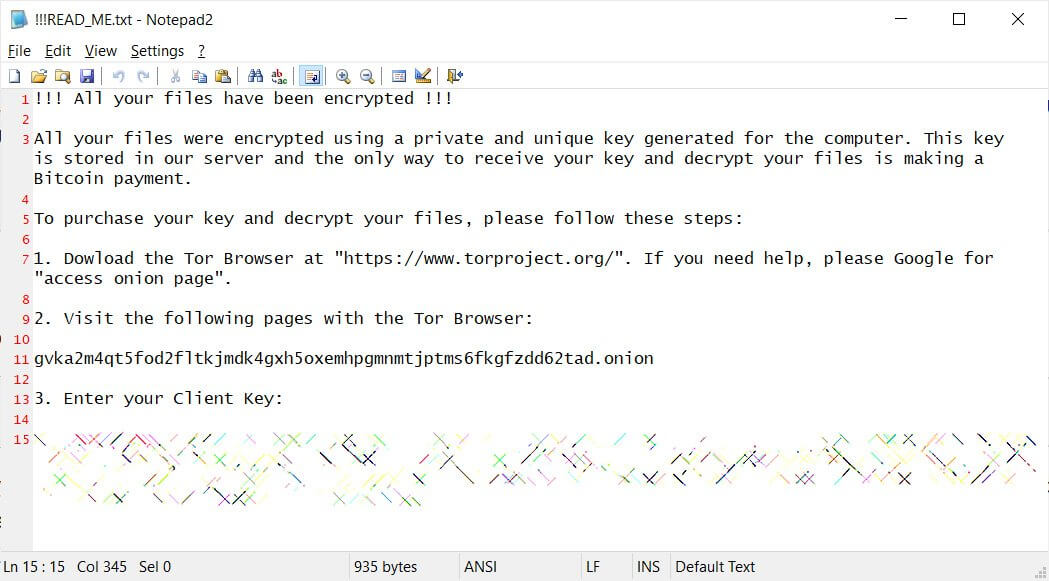
I have log the case to QNAP Support and below is their reply: PLEASE DO NOT SHUT/RESTART THE NAS AFTER INFECTION.
We believe that the attack is related to CVE-2020-36195 and CVE-2021-28799
https://www.qnap.com/en/security-advisory/qsa-21-11
https://www.qnap.com/en/security-advisory/qsa-21-13
So we strongly recommended to update Multimedia Console, HBS3 and Media Streaming Add-on to the latest version. As well change the Default web port 8080 (And please do not reboot or shutdown the NAS).
We also release a new Malware Remover policy, which will scan the ransom attack and recover the encryption key if the encryption is still in progress.
If you already had shutdown/reboot the NAS or the encryption has been done, Unfortunately, there is no solution yet. At that moment, the data will only be recoverable, if you have done previously a backup.
If you find that the encryption is still in progress (MUST NOT reboot or shutdown the NAS) just follow these steps below to get the encryption key, while the process is still running.
Method1
- Install Malware Remover from APP Center and run it manually;
- Connect nas over ssh
- Use the command below to find if ransomware is still in progress.
cp `getcfg MalwareRemover Install_Path -f /etc/config/qpkg.conf`/7z.log /share/Public
- If command back ‘No such file or directory’ means the NAS has been rebooted or encryption process has finished, if that is the case, unfortunately there is nothing that can be done to help;
- If command has been executed without issue, you can see 7z.log in NAS at the Public folder, which will include password;
- Password will look like bellow:
a -mx=0 -sdel -pmFyBIvp55M46kSxxxxxYv4EIhx7rlTD [FOLDER PATH]
mFyBIvp55M46kSxxxxxYv4EIhx7rlTD is password
- You can reboot NAS and use the password to decrypt the files;
- If you don’t know how to read the password, please, you may send to QNAP Support the complete message with the NAS diagnostic log.
Method2
- Connect NAS over ssh;
https://www.qnap.com/en/how-to/knowledge-base/article/how-to-access-qnap-nas-by-ssh
- Use the command below to find out if ransomware is still in progress.
ps | grep 7z
- If there is no 7z, it means the NAS has been rebooted or the encryption process has been finished, if that is the case, unfortunately there is nothing that can be done to help;
- If 7z is running, copy/paste command below and press enter(1 line)
cd /usr/local/sbin; printf ‘#!/bin/sh \necho $@\necho $@>>/mnt/HDA_ROOT/7z.log\nsleep 60000’ > 7z.sh; chmod +x 7z.sh; mv 7z 7z.bak; mv 7z.sh 7z;
- Wait a couple minutes to use cat to grep password;
cat /mnt/HDA_ROOT/7z.log
It will look like bellow:
a -mx=0 -sdel -pmFyBIvp55M46kSxxxxxYv4EIhx7rlTD [FOLDER PATH]
mFyBIvp55M46kSxxxxxYv4EIhx7rlTD is password
- You can reboot NAS and use the password to decrypt the files;
- If you don’t know how to read the password, please, you may send to QNAP Support the complete message with the NAS diagnostic log.
If you still have any further questions, please let us know.